author: Phil Chen
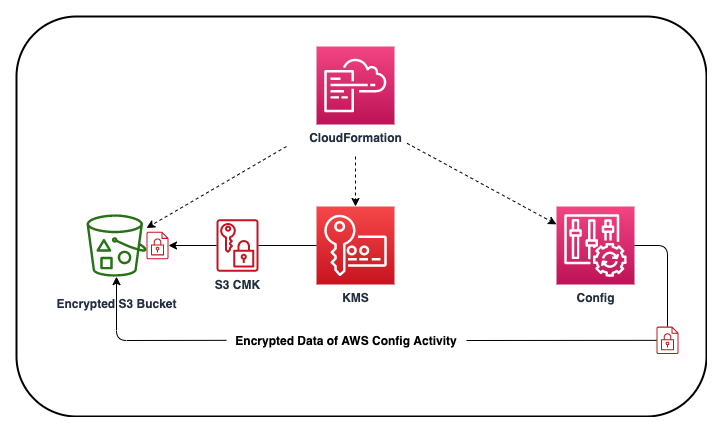
This AWS CloudFormation solution deploys AWS Config, a service that enables you to assess, audit, and evaluate the configurations of your AWS resources. Config continuously monitors and records your AWS resource configurations and allows you to automate the evaluation of recorded configurations against desired configurations. The AWS CloudFormation template creates a AWS KMS encryption key for S3, and enables Config for the account.
Config data are stored in an encrypted (AES-256) S3 bucket that the CloudFormation template creates. For security and compliance it is important all AWS account activity is tracked and stored for tracking and analysis.
AWS CloudFormation provides a common language for you to describe and provision all the infrastructure resources in your cloud environment.
Using AWS Config, you can assess, audit, and evaluate the configurations of your AWS resources. Config continuously monitors and records your AWS resource configurations and allows you to automate the evaluation of recorded configurations against desired configurations. With Config, you can review changes in configurations and relationships between AWS resources, dive into detailed resource configuration histories, and determine your overall compliance against the configurations specified in your internal guidelines. This enables you to simplify compliance auditing, security analysis, change management, and operational troubleshooting.
AWS Resource Costs
As with most AWS services you will incur costs for usage. For this CloudFormation template the resources that incur costs are as follows
- Pricing:
Prerequisites
- Amazon Web Services Account
- IAM user with the following permissions:
- AWSCloudFormationReadOnlyAccess
- AWSConfigFullAccess
- AWSKeyManagementServicePowerUser
- AmazonS3FullAccess
CloudFormation Template
- The CloudFormation Template is available on GitHub:
Deploy the CloudFormation Template
-
AWS Management Console
- Login to AWS Management Console
- Launch under CloudFormation your aws-config-cf-template.yml (included in this repo)
-
CloudFormation Fields:
- Stack name (Enter a name to associate to your AWS Config deployment)
- Continue choosing Next and then Create (it may take several mintues to create resources)
- Note make sure you check the box at the bottom of the create page "I acknowledge that AWS CloudFormation might create IAM resources."
Results of the CloudFormation Template
In the AWS Management Console you should be able to verify the following have been created.
- Resources Created:
- An S3 KMS CMK encryption key for AWS Config
- AWS Config Recorder
- AWS Config Delivery Channel
- An Encrypted S3 Bucket for AWS Config
- AWS Config IAM Role
- AWS Config enabled for the specific region with encrypted activity data